James Fallows demonstrates The Idiocy of the Shutdown, in 3 Acts: Map, Thought Experiment, Speech.
Notes from Howard's Sabbatical from Working. The name comes from a 1998 lunch conversation. Someone asked if everything man knew was on the web. I answered "no" and off the top of my head said "Fidel Castro's favorite color". About every 6-12 months I've searched for this. It doesn't show up in the first 50 Google results (this blog is finally first for that search), AskJeeves says it's: red.
Monday, September 30, 2013
Shutdown and More
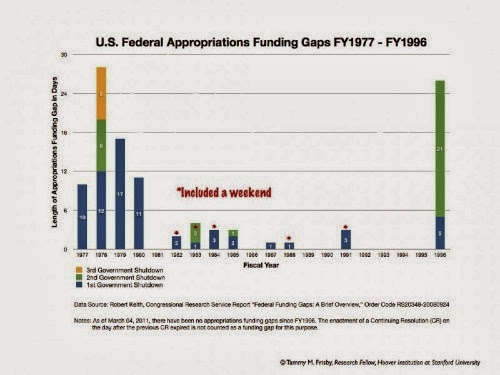
"This chart comes from Tammy Frisby of the Hoover Institution. Note that in the 1970s, gaps in funding didn't mean that the federal government had to physically shut down. That practice only started in the 1980s, after then-Attorney General Benjamin Civiletti argued that the Anti-Deficiency Act required government agencies to close up if their funding expired. Since then, a lapse in funding has meant an actual, tangible shutdown."
Washington is just broken (and yes I blame one party). Look we don't have a budget, instead we're arguing over a continuing resolution that lasts just six more weeks before we have to argue again. Kevin Drum explains Here's Why the Public Blames Republicans for an Imminent Government Shutdown
Q: Why do we need a 6-week Continuing Resolution to keep the government running?
A: Because Congress hasn't passed a budget for the new year, which begins October 1st.
Q: And why is that?
A: There's no mystery. Both the House and Senate passed budget resolutions months ago, but Paul Ryan and the rest of the GOP have refused to open talks with the Senate to negotiate a final budget number.
Q: Why is that?
A: They've been crystal clear about this. They wanted more leverage for their demands, and they figured the only way to get it was to threaten a government shutdown.
Kevin Drums says I Think Republicans Are Confused About the Word "Compromise" "So I need to ask again: what exactly do they think is the compromise here? Obviously they're trying to get something they want, but what exactly are Democrats getting in return? I don't get it. If my neighbor threatens to steal my car, and then comes back and says he'll settle for just stealing my TV set, what kind of compromise is that? What am I getting out of the deal?"
If you think the answer is avoiding a government shutdown or a worldwide economic collapse, then you are confusing negotiating with hostage taking. Remember, if the Senate bill was brought to the house floor, it would probably pass. Boehner isn't doing this (so far) to appease the tea party caucus. It's not that Democrats are unwilling to negotiate with conservatives, it's that they're unwilling to be held hostage by a minority of one half of one branch of government. If you want a stronger bargaining position, win more votes.
If you've heard of "Plan C" or the "Vitter Amendment", Ezra Klein explains it all, John Boehner’s ‘Plan C’ hurts Congress, hurts taxpayers, fixes nothing.
A bit of background is necessary here. When the Affordable Care Act was being debated in the Senate, Sen. Chuck Grassley (R-Iowa) proposed an amendment forcing members of Congress and their staffs to buy their health insurance from Obamacare's insurance marketplaces. The amendment was meant to embarrass the Democrats: The marketplaces are only for individuals. They don't allow large employers. So it wasn't really feasible for a large employer like Congress to join them.
Grassley expected Democrats to reject the amendment on technical grounds and then Republicans could say that even congressional Democrats didn't want to be part of Obamacare. It was, like Sen. Tom Coburn's (R-Okla.) silly amendment to bar Obamacare from buying Viagra for pedophiles, a press release dressed up in legislative language.
But then Democrats agreed to it.
The result was that Congress was the only large employer in the country whose employees were allowed to participate in the insurance marketplaces. And they weren't just allowed to participate in the marketplaces. They were forced to participate in the marketplaces. But there was no guidance in the legislation for how their participation in the marketplaces would work.
The way employer-sponsored insurance works is that the employer pays most of the cost. The way the exchanges work is that taxpayers subsidize people making less than 400 percent of the poverty line. But it wasn't clear if the federal government could pay for employee insurance on the Obamacare marketplaces and no one wanted taxpayers subsidizing congressional staffers.
Say we repeat this crap with raising the debt ceiling. Most people who understand this realize that is very serious. Paul Krugman tries to explain what would happen. Rebels Without a Clue.
First of all, hitting the ceiling would force a huge, immediate spending cut, almost surely pushing America back into recession. Beyond that, failure to raise the ceiling would mean missed payments on existing U.S. government debt. And that might have terrifying consequences.
Why? Financial markets have long treated U.S. bonds as the ultimate safe asset; the assumption that America will always honor its debts is the bedrock on which the world financial system rests. In particular, Treasury bills — short-term U.S. bonds — are what investors demand when they want absolutely solid collateral against loans. Treasury bills are so essential for this role that in times of severe stress they sometimes pay slightly negative interest rates — that is, they’re treated as being better than cash.
Now suppose it became clear that U.S. bonds weren’t safe, that America couldn’t be counted on to honor its debts after all. Suddenly, the whole system would be disrupted. Maybe, if we were lucky, financial institutions would quickly cobble together alternative arrangements. But it looks quite possible that default would create a huge financial crisis, dwarfing the crisis set off by the failure of Lehman Brothers five years ago.
He also throws in this, "On the economics: Republican radicals generally reject the scientific consensus on climate change; many of them reject the theory of evolution, too. So why expect them to believe expert warnings about the dangers of default? Sure enough, they don’t: the G.O.P. caucus contains a significant number of “default deniers,” who simply dismiss warnings about the dangers of failing to honor our debts."
Alpha has some more details on how the catastrophe would play out, Meet the new idiots, same as the… actually these idiots might be worse.
Remember when Republicans were worried about ‘economic uncertainty’?
The Act of Killing at Harvard on Saturday
If you haven't see The Act of Killing yet, a director's cut is playing at Harvard this Saturday, with director Joshua Oppenheimer in person.
New York City's Website Gets A Hurricane-Proof Makeover
New York City's Website Gets A Hurricane-Proof Makeover | Co.Design | business + design "nyc.gov had grown stale since its last update in 2003. Here’s how designers updated the experience, focusing on usability, especially in the face of disaster."
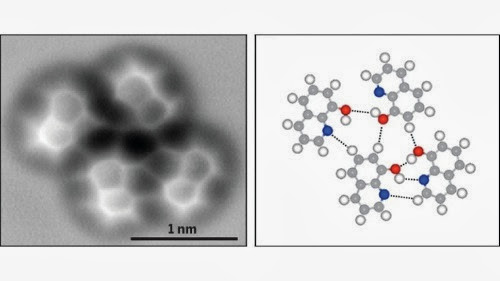
The Very First Image of a Hydrogen Bond
The Very First Image of a Hydrogen Bond "Using a technique called high-resolution atomic force microscopy (AFM), researchers in China have visualized the molecular structure of a hydrogen bond."
Bonus science image: We have seen clouds on a giant planet beyond our solar system. "By observing this planet with Spitzer and Kepler for more than three years, we were able to produce a very low-resolution 'map' of this giant, gaseous planet," said Brice-Olivier Demory of Massachusetts Institute of Technology in Cambridge. Demory is lead author of a paper accepted for publication in the Astrophysical Journal Letters. "We wouldn't expect to see oceans or continents on this type of world, but we detected a clear, reflective signature that we interpreted as clouds."
Saturday, September 28, 2013
Science trumps the Force to create a real-life lightsaber
Science trumps the Force to create a real-life lightsaber
"See, photons -- which are the elementary particles of light -- tend to be massless and kind of aloof. If you shoot two laser beams at each other, the photons just pass right through each other without so much as a hello or a high five.
But when the researchers fired a few photons into a vacuum chamber with a cloud of extremely cold rubidium atoms to take advantage of an effect called a Rydberg blockade, the photons started hanging out and even left the chamber together as the first 'photonic molecule' -- a sort of quantum bromance -- ever observed.
And it's that bond between new particle bros that creates the new form of matter, which bears a resemblance to that most awesome weapon from a galaxy far, far away.
'It's not an in-apt analogy to compare this to lightsabers,' said Harvard Professor of Physics Mikhail Lukin in a news release. 'When these photons interact with each other, they're pushing against and deflect each other. The physics of what's happening in these molecules is similar to what we see in the movies.'"
Your False-Equivalence Guide to the Days Ahead
Your False-Equivalence Guide to the Days Ahead by James Fallows is a good article with a bad headline.
"This time, the fight that matters is within the Republican party, and that fight is over whether compromise itself is legitimate.** Outsiders to this struggle -- the president and his administration, Democratic legislators as a group, voters or "opinion leaders" outside the generally safe districts that elected the new House majority -- have essentially no leverage over the outcome. I can't recall any situation like this in my own experience, and the only even-approximate historic parallel (with obvious differences) is the inability of Northern/free-state opinion to affect the debate within the slave-state South from the 1840s onward. Nor is there a conceivable "compromise" the Democrats could offer that would placate the other side."
"This isn't "gridlock." It is a ferocious struggle within one party, between its traditionalists and its radical factions, with results that unfortunately can harm all the rest of us -- and, should there be a debt default, could harm the rest of the world too. "
Friday, September 27, 2013
Meet the 2013 MacArthur Fellows
Meet the 2013 MacArthur Fellows ""
I think I've seen a story about Jeffrey Brenner's work, "creating a comprehensive health care delivery model" in Camden NJ.
I haven't heard of Jazz Pianist and Composer Vijay Iyer but Spotify has some of his music.
Thursday, September 26, 2013
Learning To Negotiate in Good Faith
I grew up in a Reform Jewish house and while we didn't go to Temple each week, we did have a Passover Seder each year. Various foods are used symbolically during the Seder and of course the most well-known is matzo. A piece of matzo known as the Afikoman is set aside during the seder before the main meal is eaten to be used for the latter part after the meal. One tradition is that children steal the Afikoman and get a reward for its return. I don't know why Jewish parents are supposed to teach their children to steal things and sell them back to the original owner, but as we practiced this I sold it back to my dad for a few dollars, something like allowance money.
I remember one year I learned that the Afikoman is required for the post-meal part of the seder. To me this meant I had infinite bargaining power over my father, because he needed something I had. So that year I asked for $1 million.
I did not get $1 million. Instead I got some amount similar to what I got every other year. Why did my genius bargaining strategy fail? I could list reasons like my dad didn't have $1 million or that he wasn't going to give that much to a child, certainly not for a piece of matzo; but the real reason was because it was ridiculous.
I think Congressional Republicans need to learn a lesson I learned when I was about 10 years old.
Anyone would expect the two parties to disagree on things in the budget. But it's another thing to constantly revisit policy that has become law, been upheld by the Supreme Court and been the centerpiece of two presidential elections. There's a reason the Democrats refer to the GOP tactics as hostage taking. Applying the same conditions on the debt ceiling is even worse. It's threatening the good faith and credit of the US and since the dollar is the world's reserve currency, a very probable global economic break down.
But now it seems that might not be all they demand. They want the entire GOP platform or else. The National Review says it obtained an outline of the GOP debt-ceiling bill. Not only does it delay Obamacare a year, it authorizes the Keystone pipeline, more oil drilling, fewer environmental regulations, weakens Dodd-Frank even more, etc. It's so extreme Ezra Klein says, "The House GOP's debt limit bill -- obtained by the National Review -- isn't a serious governing document. It's not even a plausible opening bid. It's a cry for help."
The party that talks more about faith, needs to learn what good-faith negotiating is.
The world’s first mind-controlled robotic leg is ready for prime time
io9 describes The world’s first mind-controlled robotic leg.
"Until now, the only thought-controlled prosthetics available to amputees were bionic arms. But the new leg will soon be available to the more than one million Americans with leg amputations. It was developed by lead scientist Levi Hargrove at the Rehabilitation Institute of Chicago.
The leg’s movements are controlled by a person’s original nerves, which are redirected to a small area of the thigh muscle. When these redirected nerves instruct the muscles to contract, sensors on the amputee’s leg detect tiny electrical signals from the muscles. These signals are then analyzed by a specially-designed computer program which instantaneously decodes the type of movement the patient is trying to perform (like moving the knee or ankle). It then sends these commands to the robotic leg."
Wednesday, September 25, 2013
A Trip to the Galapagos Islands
In Focus takes A Trip to the Galapagos Islands "Google Maps' Street View team recently traveled to several locations in the Galapagos Islands, snapping panoramic views as they went. Using backpack-mounted cameras and underwater gear, they documented the unique diversity of the archipelago that helped inspire Darwin's theory of evolution. The government of Ecuador established the Galapagos National Park in 1959, setting aside 97% of the islands' land area for preservation. Collected here are images from Google's team as well as from other photographers, taking you on a virtual visit to these amazing islands. [30 photos]"
Thomas Pynchon understands the power of conspiracy theories
I'm pretty sure I'm going to find this article on Thomas Pynchon's new book more interesting than his book, but I'm not going to test that. Thomas Pynchon understands the power of conspiracy theories ""
Monday, September 23, 2013
In Supreme Court Opinions, Clicks That Lead Nowhere
The New York Times wrote In Supreme Court Opinions, Clicks That Lead Nowhere
"Supreme Court opinions have come down with a bad case of link rot. According to a new study, 49 percent of the hyperlinks in Supreme Court decisions no longer work."
"For most of the Supreme Court’s history, its citations have been to static, permanent sources, typically books. Those citations allowed lawyers and scholars to find, understand and assess the court’s evidence and reasoning. Since 1996, though, justices have cited materials found on the Internet 555 times, the study found. Those citations are very often ephemeral."
"The United States Court of Appeals for the Ninth Circuit, in San Francisco, could serve as a model. It maintains an electronic archive of what it calls “webcites” in the PDF format. Professor Zittrain and his colleagues are at work on a more ambitious solution, Perma.cc, a platform built and run by a consortium of law libraries. It allows writers and editors to capture and fix transient information on the Web with a new, permanent link."
Maybe they could link to archive.org instead. If they start keeping their own copies of their cited material, I wonder how long until there's a copyright lawsuit brought. The article mentions that Scalia cited a car chase in The French Connection. Stranger things have happened than Fox suing for a clip of their content posted without their permission (even in obvious fair use situations).
Saturday, September 21, 2013
US Nearly Accidently Detonated Atomic Bomb Over North Carolina
The Guardian reports US nearly detonated atomic bomb over North Carolina
A secret document, published in declassified form for the first time by the Guardian today, reveals that the US Air Force came dramatically close to detonating an atom bomb over North Carolina that would have been 260 times more powerful than the device that devastated Hiroshima.
The document, obtained by the investigative journalist Eric Schlosser under the Freedom of Information Act, gives the first conclusive evidence that the US was narrowly spared a disaster of monumental proportions when two Mark 39 hydrogen bombs were accidentally dropped over Goldsboro, North Carolina on 23 January 1961. The bombs fell to earth after a B-52 bomber broke up in mid-air, and one of the devices behaved precisely as a nuclear weapon was designed to behave in warfare: its parachute opened, its trigger mechanisms engaged, and only one low-voltage switch prevented untold carnage.
"The document was uncovered by Schlosser as part of his research into his new book on the nuclear arms race, Command and Control. Using freedom of information, he discovered that at least 700 "significant" accidents and incidents involving 1,250 nuclear weapons were recorded between 1950 and 1968 alone."
Holy crap.
The Crazy Party
Paul Krugman describes The Crazy Party
Some pundits insist, even now, that this is somehow Mr. Obama’s fault. Why can’t he sit down with Mr. Boehner the way Ronald Reagan used to sit down with Tip O’Neill? But O’Neill didn’t lead a party whose base demanded that he shut down the government unless Reagan revoked his tax cuts, and O’Neill didn’t face a caucus prepared to depose him as speaker at the first hint of compromise.
No, this story is all about the G.O.P. First came the southern strategy, in which the Republican elite cynically exploited racial backlash to promote economic goals, mainly low taxes for rich people and deregulation. Over time, this gradually morphed into what we might call the crazy strategy, in which the elite turned to exploiting the paranoia that has always been a factor in American politics — Hillary killed Vince Foster! Obama was born in Kenya! Death panels! — to promote the same goals.
But now we’re in a third stage, where the elite has lost control of the Frankenstein-like monster it created.
So now we get to witness the hilarious spectacle of Karl Rove in The Wall Street Journal, pleading with Republicans to recognize the reality that Obamacare can’t be defunded. Why hilarious? Because Mr. Rove and his colleagues have spent decades trying to ensure that the Republican base lives in an alternate reality defined by Rush Limbaugh and Fox News. Can we say ‘hoist with their own petard’?"
Carpet Designer Threatens CosPlayers With Legal Action
Sometimes lawyers have too much time on their hands. Carpet designer threatens cosplayers with legal action.
"In the world of cosplay, people don’t generally expect to get into trouble for dressing up as well-known characters like Superman or Spock, even though the legal teams at DC Comics or Paramount could probably crush them like a bug. Unfortunately, the designers of the Marriott’s patterned carpets didn’t get the memo about turning a blind eye to cosplay tributes.
Apparently the carpet costumes were so popular that one of the original cosplayers offered a version of the Marriott carpet pattern for the presumably vast number of people who also wanted to dress up in carpet-themed camo gear. Seeing this, carpet designers Couristan Inc. sent cosplay suppliers Volpin Props a Cease & Desist letter."
Viral Political Ad
It's a little unusual for a political ad to go viral for being good. This is going around now.
Friday, September 20, 2013
The Pixar Theory
The Pixar Theory. "Every Pixar movie is connected. [Jon Negroni] explain[s] how, and possibly why."
Not infrequently people tell me I have too much free time on my hands, it's nice when I can say it of someone else.
John Boehner’s Congress is a train wreck
Ezra Klein says John Boehner’s Congress is a train wreck
Begin with the simplest question: What have they gotten done?
- The Senate managed to pass comprehensive immigration reform with bipartisan support. The House's effort has fallen apart.
- The Senate passed a farm bill. The House failed at that, and has been breaking their farm bill into pieces and trying to pass them one at a time.
- The Senate, at long last, passed a budget and moved to go to conference with the House. The House passed a budget and refused to go to conference with the Senate.
- The list goes on. Gun control was a flop. The appropriations process has been a mess. We almost went over the fiscal cliff when Boehner's 'Plan B' failed. Sequestration, which Boehner once called 'devastating,' is now the law of the land. The Fed can't pursue the policies it thinks makes sense because it's scared that Congress is going to drive the economy into a ditch."
At first I thought this wasn't quite fair. The Senate has a strong Democratic majority, so why are their objectively bills better than the House's? Well, some are bipartisan, and the Senate does have to deal with the filibuster. But then there's also the shift in positions that the House leadership has taken.
Boener said "'We ought to be judged on how many laws we repeal.' So how many laws has Boehner repealed? Well, none. He's tried to repeal Obamacare a bunch of times, but Obamacare remains the law of the land. He hasn't managed, or even really tried, to repeal any other major laws at all." Then there's his shift on sequestration, once it was unthinkable, now it's the liberal compromise.
John Boehner is being even more irresponsible than Ted Cruz
John Boehner is being even more irresponsible than Ted Cruz
The problem comes in No. 4. Boehner isn't going to simply shrug, say he tried, and bring the Senate bill to the floor. He'll shrug, say he tried, and tell his members that they should let him bring the Senate bill to the floor. He'll say it's because they need to save their fire for the debt ceiling fight, where they can force the White House to delay Obamacare for a year by threatening to trigger a global financial crisis. In fact, this is already the message he's delivering to his members.
There's been a lot of talk -- much of it among Republicans -- about how irresponsible Ted Cruz is being in his fight to defund Obamacare or shut the government down trying. But Boehner and the rest of the House GOP leadership is being much more irresponsible in their promises to delay Obamacare or cause a global financial crisis while trying. And the way they're going to get past Cruz's irresponsible threats is to double down on their own, even more irresponsible, threats.
Thursday, September 19, 2013
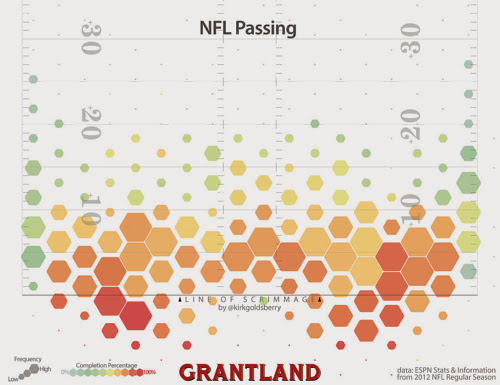
A Map of Where NFL Quarterbacks Throw the Ball
Grantland shows a Pass Atlas: A Map of Where NFL Quarterbacks Throw the Ball "Thanks to new forms of data and emerging kinds of analyses, teams, media, and fans are gaining new insights into on-field performances. I have been exploring one such data set, a giant collection of highly detailed passing data created and maintained by ESPN’s Stats & Information group."
Bonus sports infograpics from Visualizing Economics, Sports and Income
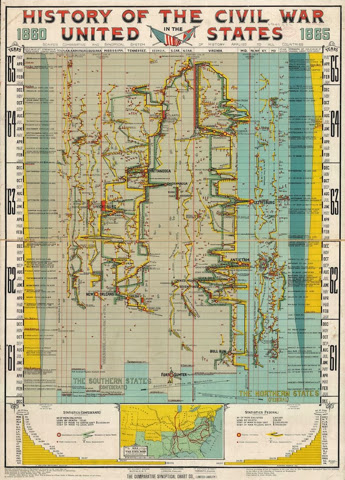
A Staggeringly Complex Infographic Of The Civil War, Drawn 116 Years Ago
A Staggeringly Complex Infographic Of The Civil War, Drawn 116 Years Ago "Once you understand the underlying gimmicks, it’s an impressive piece to be sure. The United States is broken down into a series of columns in a grand vertical timeline. In the loosest possible terms, the Union was working its way left, to Richmond, while the Confederacy worked its way right, to Washington. Yet at the same time, there were several battlefronts operating in unison, depicted in multiple side-by-side columns. And it’s these fronts the chart captures so well. The skirmish lines appear as red, while green (Confederacy) and yellow (Union) armies zigzag back and forth in a fight for territory. Presented en masse, it gives you an appreciation for both the grand choreography and futility of war--along the unparalleled patience of 19th-century data designers, who would have counted and rendered this all meticulously and macro-lessly, by hand."
The Most Spectacular Astronomy Images of the Past Year
The Most Spectacular Astronomy Images of the Past Year "There were thousands of entries this year to the Royal Observatory Greenwich's Astronomy Photographer of the Year 2013 competition. These awe inspiring images are the best of the bunch."
Colorado Flooding Photos
In Focus: Colorado Flooding: After the Deluge "Following days of record-setting rainfall and historic flooding across Colorado's Front Range, skies have cleared, and the recovery has begun. The number of people still unaccounted for has dropped to about 200, as helicopter teams are fanning out across the foothills in the largest aerial rescue operation since Hurricane Katrina in 2005. Colorado authorities coping with the aftermath are now preparing possible evacuations of prairie towns in danger of being swamped as the flood crest moves downstream. Tens of thousands of homes were damaged or destroyed, a problem exacerbated by the fact that only about 1 percent of Colorado homeowners have flood insurance. The photos below show some of the events of the past few days, following up on Monday's Historic Flooding Across Colorado. [34 photos]"
The Big Picture: Colorado floods. "The effort continued today to locate more than 500 people still missing from last week's damaging floods in Colorado. The death toll stood at 6, which state officials said is expected to rise from the heavy rains that washed out roads, collapsed bridges, destroyed homes, and left a massive clean-up in their wake. -- Lloyd Young ( 37 photos )"
Fracking may not be as bad for the climate as we thought (or it might be)
Fracking may not be as bad for the climate as we thought
So that brings us to a new peer-reviewed paper published this week in the Proceedings of the National Academy of Sciences. This study took direct measurements of 489 shale-gas wells being drilled around the United States — a far more detailed look than had been done before. (The study was conducted by the University of Texas and funded by both the Environmental Defense Fund and nine oil and gas firms, including Shell and Chevron.)
The study concluded that the methane leakage rates from these wells were fairly low — lower, in fact, than the EPA's estimates. The EPA had estimated that about 1.2 million tons of methane were probably seeping out of these wells. But the researchers found that only around 957,000 tons of methane were coming out.
What's more, the study found that new techniques required by the EPA to capture methane after wells have been drilled were very effective at minimizing certain leaks. (These techniques are known as 'green completions.') By contrast, other parts of the production process not regulated by the EPA, such as valves and chemical pumps, were leaking more methane than previously thought.
The rest of the article points out the caveats and they're significant. I think the better headline would imply that it's possible that fracking can avoid a lot of methane leaks, but we're not doing it right all the time.
What Your Taste In Music and TV Says About You On A Date
Just saw these for the first time and they're pretty funny.
What Your Taste In Music Says About You On A Date
Americans Are 110 Times More Likely to Die from Contaminated Food Than Terrorism
Alternet writes Americans Are 110 Times More Likely to Die from Contaminated Food Than Terrorism
In 2011, the year of Osama bin Laden's death, the State Department reported that 17 Americans were killed in all terrorist incidents worldwide. The same year, a single outbreak of listeriosis from tainted cantaloupe killed 33 people in the United States. Foodborne pathogens also sickened 48.7 million, hospitalized 127,839 and caused a total of 3,037 deaths. This is a typical year, not an aberration.
We have more to fear from contaminated cantaloupe than from al-Qaeda, yet the United States spends $75 billion per year spread across 15 intelligence agencies in a scattershot attempt to prevent terrorism, illegally spying on its own citizens in the process. By comparison, the Food and Drug Administration (FDA) is struggling to secure $1.1 billion in the 2014 federal budget for its food inspection program, while tougher food processing and inspection regulations passed in 2011 are held up by agribusiness lobbying in Congress. The situation is so dire that Jensen Farms, the company that produced the toxic cantaloupe that killed 33 people in 2011, had never been inspected by the FDA.
This isn't arguing that we shouldn't try to stop terrorism, it's arguing that we should pay more attention to food safety.
iOS 7
Last night I installed iOS 7 on my iPhone 5. It took about three hours as apparently everyone else was downloading it too. So far it's pretty nice. It will take me a bit to get used to the look but already Control Center is a big win. The camera is faster, background updating of apps will be nice, the calendar is much nicer and Siri seems improved. While I like that folders now have pages, my biggest complaint is that each page shows 3x3 icons instead of 4x3). I'm going to have to spend some time reorganizing my icons (but it's my fault, I have too many apps installed).
MacWorld has a good overall review, iOS 7 review: Radical redesign is more than skin-deep and The Verge has The best hidden features in iOS 7.
Update: 12 New and Hidden Settings in iOS 7.
More:
- A Few Points on iOS 7,
- iOS 7, thoroughly reviewed by Ars Technica is six pages
- iOS 7 Review and Guide by Everything iCafe is a nice overview of most things.
- First Impressions of iOS 7 for Keyboard Power Users has some cautions if you use an iPad with an external keyboard
Wednesday, September 18, 2013
Tuesday, September 17, 2013
What Has Congress Accomplished So Far
As we're about to enter several weeks of stupid budget battles I thought it might be interesting to look back at the Laws Passed by the 113th Congress so far. Of the 31 laws passed, 8 are commemorative, about 4 strike me as real (13, 24, 26, 30) regarding some fishing laws and hydropower plants and the rest seem like temporary budget fixes and dumb fixes to austerity laws (9 was the airline fix) and other things. Pretty weak.
Public Law 113-1 Passed Congress as bill H.R. 41 Signed into law by the President 1/6/2013.
- To temporarily increase the borrowing authority of the Federal Emergency Management Agency for carrying out the National Flood Insurance Program.
Public Law 113-2 Passed Congress as bill H.R. 152 Signed into law by the President 1/29/2013.
- "Sandy Recovery Improvement Act of 2013"
Public Law 113-3 Passed Congress as bill H.R. 325 Signed into law by the President 2/4/2013.
- To ensure the complete and timely payment of the obligations of the United States Government until May 19, 2013, and for other purposes.
Public Law 113-4 Passed Congress as bill S. 47 Signed into law by the President 3/7/2013.
- "Violence Against Women Reauthorization Act of 2013"
Public Law 113-5 Passed Congress as bill H.R. 307 Signed into law by the President 3/13/2013.
- "Pandemic and All-Hazards Preparedness Reauthorization Act of 2013"
Public Law 113-6 Passed Congress as bill H.R. 933 Signed into law by the President 3/26/2013.
- "Consolidated and Further Continuing Appropriations Act, 2013"
Public Law 113-7 Passed Congress as bill S. 716 Signed into law by the President 4/15/2013.
- A bill to modify the requirements under the STOCK Act regarding online access to certain financial disclosure statements and related forms.
Public Law 113-8 Passed Congress as bill H.R. 1246 Signed into law by the President 5/1/2013.
- "District of Columbia Chief Financial Officer Vacancy Act"
- To amend the District of Columbia Home Rule Act to provide that the District of Columbia Treasurer or one of the Deputy Chief Financial Officers of the Office of the Chief Financial Officer of the District of Columbia may perform the functions and duties of the Office in an acting capacity if there is a vacancy in the Office.
Public Law 113-9 Passed Congress as bill H.R. 1765 Signed into law by the President 5/1/2013.
- "Reducing Flight Delays Act of 2013"
- To provide the Secretary of Transportation with the flexibility to transfer certain funds to prevent reduced operations and staffing of the Federal Aviation Administration, and for other purposes.
Public Law 113-10 Passed Congress as bill H.R. 1071 Signed into law by the President 5/17/2013.
- To specify the size of the precious-metal blanks that will be used in the production of the National Baseball Hall of Fame commemorative coins.
Public Law 113-11 Passed Congress as bill H.R. 360 Signed into law by the President 5/24/2013.
- To award posthumously a Congressional Gold Medal to Addie Mae Collins, Denise McNair, Carole Robertson, and Cynthia Wesley, in recognition of the 50th commemoration of the bombing of the Sixteenth Street Baptist Church where the 4 little Black girls lost their lives, which served as a catalyst for the Civil Rights Movement.
Public Law 113-12 Passed Congress as bill H.R. 258 Signed into law by the President 6/3/2013.
- "Stolen Valor Act of 2013"
- To amend title 18, United States Code, with respect to fraudulent representations about having received military declarations or medals.
Public Law 113-13 Passed Congress as bill S. 982 Signed into law by the President 6/3/2013.
- "Freedom to Fish Act"
- A bill to prohibit the Corps of Engineers from taking certain actions to establish a restricted area prohibiting public access to waters downstream of a dam, and for other purposes.
Public Law 113-14 Passed Congress as bill S. 622 Signed into law by the President 6/13/2013.
- "Animal Drug and Animal Generic Drug User Fee Reauthorization Act of 2013"
- An original bill to amend the Federal Food, Drug, and Cosmetic Act to reauthorize user fee programs relating to new animal drugs and generic new animal drugs.
Public Law 113-15 Passed Congress as bill H.R. 475 Signed into law by the President 6/25/2013.
- To amend the Internal Revenue Code of 1986 to include vaccines against seasonal influenza within the definition of taxable vaccines.
Public Law 113-16 Passed Congress as bill H.R. 324 Signed into law by the President 7/12/2013.
- To grant the Congressional Gold Medal, collectively, to the First Special Service Force, in recognition of its superior service during World War II.
Public Law 113-17 Passed Congress as bill H.R. 1151 Signed into law by the President 7/12/2013.
- To direct the Secretary of State to develop a strategy to obtain observer status for Taiwan at the triennial International Civil Aviation Organization Assembly, and for other purposes.
Public Law 113-18 Passed Congress as bill H.R. 2383 Signed into law by the President 7/12/2013.
- To designate the new Interstate Route 70 bridge over the Mississippi River connecting St. Louis, Missouri, and southwestern Illinois as the "Stan Musial Veterans Memorial Bridge".
Public Law 113-19 Passed Congress as bill H.R. 251 Signed into law by the President 7/18/2013.
- "South Utah Valley Electric Conveyance Act" To direct the Secretary of the Interior to convey certain Federal features of the electric distribution system to the South Utah Valley Electric Service District, and for other purposes.
Public Law 113-20 Passed Congress as bill H.R. 254 Signed into law by the President 7/18/2013.
- "Bonneville Unit Clean Hydropower Facilitation Act" To authorize the Secretary of the Interior to facilitate the development of hydroelectric power on the Diamond Fork System of the Central Utah Project.
Public Law 113-21 Passed Congress as bill H.R. 588 Signed into law by the President 7/18/2013.
- "Vietnam Veterans Donor Acknowledgment Act of 2013" To provide for donor contribution acknowledgments to be displayed at the Vietnam Veterans Memorial Visitor Center, and for other purposes.
Public Law 113-22 Passed Congress as bill H.R. 2289 Signed into law by the President 7/25/2013.
- To rename section 219(c) of the Internal Revenue Code of 1986 as the Kay Bailey Hutchison Spousal IRA.
Public Law 113-23 Passed Congress as bill H.R. 267 Signed into law by the President 8/9/2013.
- "Hydropower Regulatory Efficiency Act of 2013" To improve hydropower, and for other purposes.
Public Law 113-24 Passed Congress as bill H.R. 678 Signed into law by the President 8/9/2013.
- "Bureau of Reclamation Small Conduit Hydropower Development and Rural Jobs Act" To authorize all Bureau of Reclamation conduit facilities for hydropower development under Federal Reclamation law, and for other purposes.
Public Law 113-25 Passed Congress as bill H.R. 1092 Signed into law by the President 8/9/2013.
- To designate the air route traffic control center located in Nashua, New Hampshire, as the "Patricia Clark Boston Air Route Traffic Control Center".
Public Law 113-26 Passed Congress as bill H.R. 1171 Signed into law by the President 8/9/2013.
- "Formerly Owned Resources for Veterans to Express Thanks for Service (FOR VETS) Act of 2013" To amend title 40, United States Code, to improve veterans service organizations access to Federal surplus personal property.
Public Law 113-27 Passed Congress as bill H.R. 1344 Signed into law by the President 8/9/2013.
- "Helping Heroes Fly Act"
- To amend title 49, United States Code, to direct the Assistant Secretary of Homeland Security (Transportation Security Administration) to provide expedited air passenger screening to severely injured or disabled members of the Armed Forces and severely injured or disabled veterans, and for other purposes.
Public Law 113-28 Passed Congress as bill H.R. 1911 Signed into law by the President 8/9/2013.
- "Bipartisan Student Loan Certainty Act of 2013"
- To amend the Higher Education Act of 1965 to establish interest rates for new loans made on or after July 1, 2013, to direct the Secretary of Education to convene the Advisory Committee on Improving Postsecondary Education Data to conduct a study on improvements to postsecondary education transparency at the Federal level, and for other purposes.
Public Law 113-29 Passed Congress as bill H.R. 2167 Signed into law by the President 8/9/2013.
- "Reverse Mortgage Stabilization Act of 2013"
- To authorize the Secretary of Housing and Urban Development to establish additional requirements to improve the fiscal safety and soundness of the home equity conversion mortgage insurance program.
Public Law 113-30 Passed Congress as bill H.R. 2576 Signed into law by the President 8/9/2013.
- To amend title 49, United States Code, to modify requirements relating to the availability of pipeline safety regulatory documents, and for other purposes.
Public Law 113-31 Passed Congress as bill H.R. 2611 Signed into law by the President 8/9/2013.
- To designate the headquarters building of the Coast Guard on the campus located at 2701 Martin Luther King, Jr., Avenue Southeast in the District of Columbia as the "Douglas A. Munro Coast Guard Headquarters Building", and for other purposes.
Monday, September 16, 2013
With 30 tuners and 30 TB of storage, SnapStream makes TiVos look like toys
I'm pretty happy with my new 3TB 6 tuner TiVo Roamio but Ars Technica writes With 30 tuners and 30 TB of storage, SnapStream makes TiVos look like toys.
"Houston-based SnapStream makes a line of DVRs that scale to truly silly sizes—its products are the monster trucks of the DVR world. If you watch TV at all, you've almost certainly already seen what SnapStream can do—popular shows like The Colbert Report, The Daily Show, The Soup, and tons of others are customers, using 30+ channel DVRs to record dozens and dozens of TV shows simultaneously in order to integrate clips from those recorded shows into their own."
Imagine this: In Germany, one TV ad per candidate
Emily Schultheis wrote in Politico Imagine this: In Germany, one TV ad per candidate. "And instead of myriad ads on different topics featuring different people, each party in Germany typically releases just one main minute-and-a-half ad for the entire election."
Part of the reason for the stark difference in TV advertising is the way German system works: each party is allotted a certain amount of airtime on the two public TV networks, ZDF and ARD, based on their vote share in the last election and the number of members in their party.
For the major parties, the CDU and the SPD, that’s eight times on each channel — over the entire course of the campaign. Ads for the smaller parties — the Greens, the Free Democratic Party and the Left Party — will run four times each on ARD and ZDF.
Parties can buy additional spots on private television channels, though their limited campaign budgets keep them from spending anywhere close to the level of U.S. candidates. President Barack Obama and GOP candidate Mitt Romney ran billion-dollar campaigns last year; in Germany, by contrast, each of the major parties expects to spend about $26 to 33 million for the entire campaign.
I wonder what would happen if we banned TV ads in elections? Candidates could still get their message out via newspapers and the Internet. They'd save millions and in presidential elections billions of dollars. Politicians would have to fundraise less (which is about a third of their time now) and wealthy donors (individuals and corporations) would have less influence over them (and might save money). Networks would make more money because they have to offer some airtime at a reduced rate for elections. I'm really not seeing a downside.
Lunar Laser Communications Demonstration
That rocket launch from Virginia the other week included an experiment known as LLCD or Lunar Laser Communications Demonstration.
The main goal of LLCD is proving fundamental concepts of laser communications and transferring data at a rate of 622 megabits per second (Mbps), which is about five times the current state-of-the-art from lunar distances. Engineers expect future space missions to benefit greatly from the use of laser communications technology. This new ability will provide increased data transmission for real-time communication and 3-D high-definition video, while taking advantage of its lower on-orbit mass and power requirements. For example, using S-band communications, the LADEE spacecraft would take 639 hours to download an average-length HD movie. Using LLCD technology, download times will be reduced to less than eight minutes."
40 maps that explain the world
The Washington Post blog WorldViews posted 40 maps that explain the world "Maps can be a remarkably powerful tool for understanding the world and how it works, but they show only what you ask them to. So when we saw a post sweeping the Web titled '40 maps they didn't teach you in school,' one of which happens to be a WorldViews original, I thought we might be able to contribute our own collection. Some of these are pretty nerdy, but I think they're no less fascinating and easily understandable. A majority are original to this blog (see our full maps coverage here), with others from a variety of sources. I've included a link for further reading on close to every one."
Number nine had some surprises for me:
Why is the U.S.’s 1 percent so much richer than everywhere else?
Why is the U.S.’s 1 percent so much richer than everywhere else? "That's the focus of this month's Journal of Economic Perspectives, which features several papers arguing a few sides of the debate, offering some fascinating windows into the nature of extreme wealth. Increasing income inequality is not disputed. The question of why the divide is widening, though, splits economists into two broad camps. One believes that people at the top have used their positions of influence to lock in excessive earnings. The other thinks that people with scarce and unique talents have simply been able to command a premium in markets that have gotten bigger over time."
$700k windfall: Russian man outwits bank with hand-written credit contract
$700k windfall: Russian man outwits bank with hand-written credit contract. I really do love stories like this. Reminds me of the guy that bought a Dell to use Linux on, read the Windows license, didn't agree to the terms and followed their instructions to destroy all copies and return for a full refund. Dell had no idea what to do and said go to Microsoft. MS said you have to go to Dell. Ultimately he won.
A Russian man who decided to write his own small print in a credit card contract has had his changes upheld in court. He's now suing the country's leading online bank for more than 24 million rubles ($727,000) in compensation.
Disappointed by the terms of the unsolicited offer for a credit card from Tinkoff Credit Systems in 2008, a 42-year-old Dmitry Agarkov from the city of Voronezh decided to hand write his own credits terms.
The trick was that Agarkov simply scanned the bank’s document and ‘amended’ the small print with his own terms.
He opted for a 0 percent interest rate and no fees, adding that the customer 'is not obliged to pay any fees and charges imposed by bank tariffs.' The bank, however, didn’t read ‘the amendments’, as it signed and certified the document, as well as sent the man a credit card. Under the agreement, the bank OK'd to provide unlimited credit, according to Agarkov’s lawyer Dmitry Mikhalevich talking to Kommersant daily.
Is Google Funding Climate Science Denial?
Back in July Think Progress wrote Is Google Funding Climate Science Denial? Jim Inhofe Fundraiser Planned For July 11
Google’s motto is ‘Don’t Be Evil,’ but it is supporting one of the worst deniers of climate science in the world: Sen. Jim Inhofe (R-OK). On July 11, Google is hosting a lunchtime $250-$2500 a plate fundraiser for Inhofe with the National Republican Senatorial Committee at its Washington, DC headquarters at 1101 New York Ave NW.
The Washington Post also recently revealed that Google was the biggest single donor to the Competitive Enterprise Institute’s annual dinner on Thursday, June 20, dropping $50,000 in support of this anti-science group. The dinner was headlined by radical global warming denier Sen. Rand Paul. CEI’s other donors include a who’s who of polluters: American Coalition for Clean Coal Electricity, Altria (Phillip Morris), Koch Companies, and Koch’s Americans For Prosperity. CEI is famed for its ad promoting carbon dioxide emissions: ‘They call it pollution. We call it life.’
I'm not sure what came of it but if true, I'm not happy about it.
The Talented Justice Kagan
Back in June, the New York Times wrote about The Talented Justice Kagan "I have been writing about the court the past three terms, and reading her prose has been as enjoyable as watching her in action. No previous justice has written with her emphasis on the vernacular or so matter-of-factly addressed readers as if our views about a case truly mattered. In a dissent this term about a labor dispute resolved on a technicality, which unfairly deprived the plaintiff of her day in court, she wrote, ‘The court today resolves an imaginary question, based on a mistake the courts below made about this case and others like it.’ She added, ‘Feel free to relegate the majority’s decision to the furthest reaches of your mind: The situation it addresses should never again rise.’"
Thursday, September 12, 2013
Russia’s position on Syria is all about constraining America
Brad Plummer talks with Dmitri Trenin, Russia’s position on Syria is all about constraining America
At a minimum Russia wants to achieve U.S. non-intervention in Syria. The medium-term goal here, although it’s pretty high up, is resolution of the Syrian issue, with some kind of political resolution. But the larger goal, the really big goal is forcing the United States back into the U.N. Security Council-centered international system.
There were many things that struck me in that op-ed, an it’s hard to deconstruct or summarize in a sentence. I think Putin is basically saying something that a lot of people will find objectionable — that the United States has been soaring above international law and it’s time the country to return inside the framework of international law as codified by the United Nations charter, especially with the Security Council."
I didn't know this:
Syria is marginally important. It’s important as a market for Russian arms. But Russia is not involved in the geopolitics of the Middle East the way the Soviet Union was, so Syria’s not important as a foothold in geopolitical terms. There are some other things like the Tartus naval facility [a naval station in Syria and Russia's only resupply spot on the Mediterranean], but I would say they are relatively marginal in Russia’s thinking here.
A government shutdown just became a bit more likely. That might be a good thing.
Ezra Klein explains A government shutdown just became a bit more likely. That might be a good thing. It's an utter mess. Read the whole thing, it's short, but some examples:
"2) The GOP’s small Obamacare problem. The vote was delayed because the House GOP can’t decide on what to do about Obamacare. Hardcore conservatives want to refuse to fund the government as long as any of that funding goes to Obamacare — which is to say, they want to shut down the government over Obamacare. This is a fight that House leadership believes they will lose, and lose very badly.
So Team Boehner tried to finesse it. The funding bill required a vote on defunding Obamacare. But House conservatives quickly realized that they would lose the vote in the Senate and the result would be the federal government would get funded, and Obamacare would be funded along with it. So they turned on the bill, and, fearing for its passage, House leadership delayed the vote."
"Meanwhile, time is running short. As Jonathan Chait writes, “a bill needs to pass by September 30, and Congress has a rigorous vacation schedule to adhere to, giving it precious little time to accomplish the goal of not shutting down the government.”"
"Meanwhile, time is running short. As Jonathan Chait writes, “a bill needs to pass by September 30, and Congress has a rigorous vacation schedule to adhere to, giving it precious little time to accomplish the goal of not shutting down the government.”"
Wednesday, September 11, 2013
Security of Java takes a dangerous turn for the worse
I haven't had Java installed on my machines in a while but as a former Java programmer this is a bit depressing, Security of Java takes a dangerous turn for the worse, experts say
"The most visible sign of deterioration are in-the-wild attacks exploiting unpatched vulnerabilities in Java version 6, Christopher Budd, threat communications manager at antivirus provider Trend Micro, wrote in a blog post published Tuesday. The version, which Oracle stopped supporting in February, is still used by about half of the Java user base, he said. Malware developers have responded by reverse engineering security patches issued for Java 7, and using the insights to craft exploits for the older version. Because Java 6 is no longer supported, the security those same flaws will never be fixed."
No Edge 2: The Curvature of the Universe
Zogg the Alien is back and is explaining the curvature of space. I posted part 1 in July. Part 2 lost me a little about two-thirds of the way in, but it's the best explanation I've seen of topology concepts.
Abrupt rise of new machine ecology beyond human response time
Here's an interesting new paper on high frequency trading, treating it as a "machine ecology" Abrupt rise of new machine ecology beyond human response time. The abstract:
Society's techno-social systems are becoming ever faster and more computer-orientated. However, far from simply generating faster versions of existing behaviour, we show that this speed-up can generate a new behavioural regime as humans lose the ability to intervene in real time. Analyzing millisecond-scale data for the world's largest and most powerful techno-social system, the global financial market, we uncover an abrupt transition to a new all-machine phase characterized by large numbers of subsecond extreme events. The proliferation of these subsecond events shows an intriguing correlation with the onset of the system-wide financial collapse in 2008. Our findings are consistent with an emerging ecology of competitive machines featuring ‘crowds’ of predatory algorithms, and highlight the need for a new scientific theory of subsecond financial phenomena.
io9 has an article about that is more approachable (I didn't read the paper), A new digital ecology is evolving, and humans are being left behind.
Tuesday, September 10, 2013
Monday, September 09, 2013
Vote on New MBTA Map
MBTA System Maps Competition 2013 "This past spring, the MBTA launched the New Perspectives MBTA Map Re-design competition. The response was overwhelming, not only because of the dozens of responses received, but the impressive quality of many of the entries. A panel of experts including the MBTA, academics, urban planners, and mapping aficionados evaluated each of the entries against a set of criteria. The six maps below were the highest rated.
Please vote on the six finalist in our System Maps Competition survey."
I liked number four.
Sunday, September 08, 2013
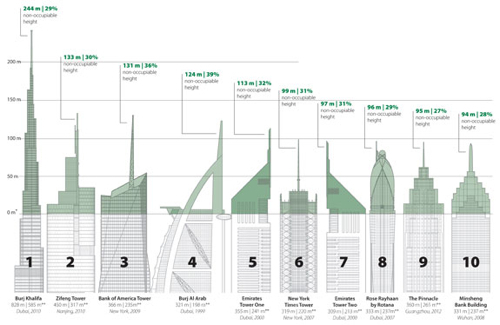
Vanity Height of Tall Buildings
Tall Buildings In Numbers Vanity Height "We noticed in Journal 2013 Issue I’s case study on Kingdom Tower, Jeddah, that a fair amount of the top of the building seemed to be an unoccupied spire. This prompted us to investigate the increasing trend towards extreme spires and other extensions of tall buildings that do not enclose usable space, and create a new term to describe this – Vanity Height, i.e., the distance between a skyscraper’s highest occupiable floor and its architectural top, as determined by CTBUH Height Criteria."
A bunch of interesting infographics at the site.
Saturday, September 07, 2013
Un Conte
This two minute animated short is really good. Powerful, with something to say and a bit unexpected.
It's French, and Un Conte translates to A Tale and let me remind you that it's French and not Pixar.
Un Conte from GOBELINS pro on Vimeo.
Is there an alternative to bombing Syria? Rep. Chris Smith thinks so.
Is there an alternative to bombing Syria? Rep. Chris Smith (R-NY) thinks so.
"The House Republican from New Jersey introduced a bill Wednesday to set up a Syrian war crimes tribunal as an alternative to missile strikes against Bashar Assad’s government. Smith’s resolution would call for an immediate ceasefire in Syria and direct the president to work with the United Nations to set up a tribunal to investigate war crimes committed by both the Syrian government and rebel groups in the country."
This does sound pretty good. I'm not sure it would work, but it does seem reasonable enough to try with little downside.
Friday, September 06, 2013
Scenes From 21st-Century China
In Focus shows Scenes From 21st-Century China "The People's Republic of China, the most populous country, and the second-largest economy, in the world, is a vast, dynamic nation that continues to grow and evolve. In this, the latest entry in a semi-regular series on China, we find a tremendous variety of images, including an earthquake in Gansu province, a massive rubber duck in Beijing, a narrow five-story nail house, and a replica of Paris -- complete with an Eiffel Tower. This collection offers only a small view of people and places across the country over the past few months. [40 photos]"
I'd include a photo, but it's the variety and some of the juxtapositions that make it interesting.
The Truth of Fact, the Truth of Feeling by Ted Chiang
Subterranean Press published a new short story by Ted Chiang: The Truth of Fact, the Truth of Feeling. It's an interesting read comparing the future of digital augmented memory to the introduction of writing.
Obamacare Premiums and Rate Shock: New studies and a Consensus
Jonathan Cohn has a really good article in The New Republic, Obamacare Premiums and Rate Shock: New studies and a Consensus.
Thursday, September 05, 2013
Recent NSA Revelations
I haven't written much about the NSA scandals because there's so much written about it and I've fallen behind. Here's an attempt to catch up on some recent stuff. If you're only going to read one article, just jump to the bottom and read this one.
On July 31st, Glenn Greenwald wrote about XKeyscore: NSA tool collects 'nearly everything a user does on the internet'
"A top secret National Security Agency program allows analysts to search with no prior authorization through vast databases containing emails, online chats and the browsing histories of millions of individuals, according to documents provided by whistleblower Edward Snowden."
"But training materials for XKeyscore detail how analysts can use it and other systems to mine enormous agency databases by filling in a simple on-screen form giving only a broad justification for the search. The request is not reviewed by a court or any NSA personnel before it is processed. XKeyscore, the documents boast, is the NSA's "widest reaching" system developing intelligence from computer networks – what the agency calls Digital Network Intelligence (DNI). One presentation claims the program covers "nearly everything a typical user does on the internet", including the content of emails, websites visited and searches, as well as their metadata."
"The XKeyscore system is continuously collecting so much internet data that it can be stored only for short periods of time. Content remains on the system for only three to five days, while metadata is stored for 30 days. One document explains: "At some sites, the amount of data we receive per day (20+ terabytes) can only be stored for as little as 24 hours." To solve this problem, the NSA has created a multi-tiered system that allows analysts to store "interesting" content in other databases, such as one named Pinwale which can store material for up to five years."
My sense is, they sweep up everything they can and then do searches when asked. They are legally limited in what they are allowed to collect (i.e., not from Americans) but they use the tree falling in the forest analogy. If they collect it and no one looks at it, is it really collected. So they say the information is only collected if it is ever returned in a search.
To me the problem is that they've basically constructed a time machine. They keep everything you do online for some period of time and can go back and look through it. Now the philosophical question is, do you change your behavior if you know it's being recorded? I think the answer is yes. On CBS This Morning today I saw a piece about how when businesses monitor employees performance with real metrics, the employees work harder (to avoid being fired). Lawyers sometimes prefer talking to their clients on particular topics rather than via email to avoid having a specific record or businesses do it to avoid secrets being found out in discovery.
On another point, based on how Snowden was able to get this info, it seems the NSA systems have crappy internal security. If you have some clearance you can query anything you want and system administrators have full access. It needn't and shouldn't be that way. There seem to examples where NSA analysts used the system to find out info about romantic interests. They were disciplined but a truly secure system wouldn't allow a user to do such a thing in the first place (imagine having to enter a subpoena number before doing a query).
John Naughton sums this up nicely. Edward Snowden's not the story. The fate of the internet is. "The press has lost the plot over the Snowden revelations. The fact is that the net is finished as a global network and that US firms' cloud services cannot be trusted"
So as a public service, let us summarise what Snowden has achieved thus far. Without him, we would not know how the National Security Agency (NSA) had been able to access the emails, Facebook accounts and videos of citizens across the world; or how it had secretly acquired the phone records of millions of Americans; or how, through a secret court, it has been able to bend nine US internet companies to its demands for access to their users' data.
Similarly, without Snowden, we would not be debating whether the US government should have turned surveillance into a huge, privatised business, offering data-mining contracts to private contractors such as Booz Allen Hamilton and, in the process, high-level security clearance to thousands of people who shouldn't have it. Nor would there be – finally – a serious debate between Europe (excluding the UK, which in these matters is just an overseas franchise of the US) and the United States about where the proper balance between freedom and security lies.
He goes on to ask bigger questions. Will the Internet break up into regional divisions? Given the revelations about what the US government is doing, will they continue to have as big a role as they do in Internet governance? Will foreign people and companies trust US cloud services (like Google, Facebook, Yahoo, Amazon, Apple, Microsoft, etc) with their information?
James Fallows correctly points out, Why NSA Surveillance Will Be More Damaging Than You Think. "The real threat from terrorism has never been the damage it does directly, even through attacks as horrific as those on 9/11. The more serious threat comes from the over-reaction, the collective insanity or the simple loss of perspective, that an attack evokes. Our government's ambition to do everything possible to keep us "safe" has put us at jeopardy in other ways."
So to try to improve their image the Director of the NSA spoke at the annual Black Hat security conference. That's a rare event. Also as Spencer Ackerman explains, US government declassifies court order on NSA surveillance as pressure builds.
"Clearly Congress intended for Section 215 of the Patriot Act to be a tool for investigating terrorists and spies, not for tracking the communications of all Americans. No prosecutor would seek a grand jury subpoena of this scope and no judge in a criminal or civil procedure would enforce one."
A proposed change to system sounds reasonable to me. US senators push for special privacy advocate in overhauled Fisa court
Senators Richard Blumenthal of Connecticut, Ron Wyden of Oregon and Tom Udall of New Mexico, all Democrats, want a special advocate for Americans' privacy to argue before the so-called Fisa court when the government seeks extraordinary surveillance requests. They also propose to diversify the powerful secret court ideologically and geographically.
A few days ago we found out about the secret budget of these agencies.
The Washington Post wrote, ‘Black budget’ summary details U.S. spy network’s successes, failures and objectives.
The $52.6 billion “black budget” for fiscal 2013, obtained by The Washington Post from former intelligence contractor Edward Snowden, maps a bureaucratic and operational landscape that has never been subject to public scrutiny. Although the government has annually released its overall level of intelligence spending since 2007, it has not divulged how it uses the money or how it performs against the goals set by the president and Congress. The 178-page budget summary for the National Intelligence Program details the successes, failures and objectives of the 16 spy agencies that make up the U.S. intelligence community, which has 107,035 employees.
Historical data on U.S. intelligence spending is largely nonexistent. Through extrapolation, experts have estimated that Cold War spending probably peaked in the late 1980s at an amount that would be the equivalent of $71 billion today. Spending in the most recent cycle surpassed that amount, based on the $52.6 billion detailed in documents obtained by The Post plus a separate $23 billion devoted to intelligence programs that more directly support the U.S. military.
They've got a big infographic. The Black Budget: Top secret U.S. intelligence funding. WonkBlog loves graphs so they broke down, America’s secret intelligence budget, in 11 (nay, 13) charts.
Via these documents we learned, U.S. spy agencies mounted 231 offensive cyber-operations in 2011. "Additionally, under an extensive effort code-named GENIE, U.S. computer specialists break into foreign networks so that they can be put under surreptitious U.S. control. Budget documents say the $652 million project has placed “covert implants,” sophisticated malware transmitted from far away, in computers, routers and firewalls on tens of thousands of machines every year, with plans to expand those numbers into the millions."
The administration’s cyber-operations sometimes involve what one budget document calls “field operations” abroad, commonly with the help of CIA operatives or clandestine military forces, “to physically place hardware implants or software modifications.”
Much more often, an implant is coded entirely in software by an NSA group called Tailored Access Operations (TAO). As its name suggests, TAO builds attack tools that are custom-fitted to their targets.
The NSA unit’s software engineers would rather tap into networks than individual computers because there are usually many devices on each network. Tailored Access Operations has software templates to break into common brands and models of “routers, switches and firewalls from multiple product vendor lines,” according to one document describing its work.
The implants that TAO creates are intended to persist through software and equipment upgrades, to copy stored data, “harvest” communications and tunnel into other connected networks. This year TAO is working on implants that “can identify select voice conversations of interest within a target network and exfiltrate select cuts,” or excerpts, according to one budget document. In some cases, a single compromised device opens the door to hundreds or thousands of others.
Sometimes an implant’s purpose is to create a back door for future access. “You pry open the window somewhere and leave it so when you come back the owner doesn’t know it’s unlocked, but you can get back in when you want to,” said one intelligence official, who was speaking generally about the topic and was not privy to the budget. The official spoke on the condition of anonymity to discuss sensitive technology.
Under U.S. cyberdoctrine, these operations are known as “exploitation,” not “attack,” but they are essential precursors both to attack and defense.
By the end of this year, GENIE is projected to control at least 85,000 implants in strategically chosen machines around the world. That is quadruple the number — 21,252 — available in 2008, according to the U.S. intelligence budget.
The NSA appears to be planning a rapid expansion of those numbers, which were limited until recently by the need for human operators to take remote control of compromised machines. Even with a staff of 1,870 people, GENIE made full use of only 8,448 of the 68,975 machines with active implants in 2011.
For GENIE’s next phase, according to an authoritative reference document, the NSA has brought online an automated system, code-named TURBINE, that is capable of managing “potentially millions of implants” for intelligence gathering “and active attack.”
The Washington Post followed up with The NSA has its own team of elite hackers.
But for all the reported secrecy surrounding TAO’s activities, a quick search of networking site LinkedIn shows a number of current and former intelligence community employees talking pretty openly about the exploits.
For instance, Brendan Conlon, whose page lists him as a former Deputy Chief of Integrated Cyber Operations for the NSA and former Chief of TAO in Hawaii, says that he led “a large group of joint service NSA civilians and contractors in executing Computer Network Exploitation (CNE) operations against target networks.” Barbara Hunt, who is listed as a former Director of Capabilities at TAO in Fort Meade, similarly claims she was “responsible for end-to-end development and capability delivery to build a versatile computer network exploitation effort.”
Dean Schyvincht, who claims to currently be a TAO Senior Computer Network Operator in Texas, might reveal the most about the scope of TAO activities. He says the 14 personnel under his management have completed “over 54,000 Global Network Exploitation (GNE) operations in support of national intelligence agency requirements.” Just imagine how productive the team in Fort Meade, rumored to have about 600 people, must be.
I wish Neal Stephenson would write a novel about these people.
Via one of the budget line items we've learned and Wired explores, Feds plow resources into “groundbreaking” crypto-cracking program.
The document goes on to reveal that something called the Consolidated Cryptologic Program has received more than $10 billion annually for the past four years, and it employs about 35,000 people. It also shows that 23 percent of this year's program funding supported collection and operations, 15 percent went to processing and exploitation, and 14 percent funded analysis and production. In addition to supporting cracking, the $10 billion presumably includes funding for so-called comsec, short for communications security, which is designed to prevent adversaries from accessing communications in an intelligible form.
One of the items computer security people are speculating about is Groundbreaking NSA Crypto-Cracking. The documents include a summary by Director of National Intelligence James Clapper.
“Also,” Clapper writes in a line marked “top secret,” “we are investing in groundbreaking cryptanalytic capabilities to defeat adversarial cryptography and exploit internet traffic.” The Post’s article doesn’t detail the “groundbreaking cryptanalytic capabilities” Clapper mentions, and there’s no elaboration in the portion of the document published by the paper. But the document shows that 21 percent of the intelligence budget — around $11 billion — is dedicated to the Consolidated Cryptologic Program that staffs 35,000 employees in the NSA and the armed forces.
Yesterday Bruce Schneier speculated, What Exactly Are the NSA's 'Groundbreaking Cryptanalytic Capabilities'?.
Honestly, I’m skeptical. Whatever the NSA has up its top-secret sleeves, the mathematics of cryptography will still be the most secure part of any encryption system. I worry a lot more about poorly designed cryptographic products, software bugs, bad passwords, companies that collaborate with the NSA to leak all or part of the keys, and insecure computers and networks. Those are where the real vulnerabilities are, and where the NSA spends the bulk of its efforts.
He speculates they might have some attacks against symmetric cryptography the way they had differential cryptanalysis before academia did but isn't too worried about that.
So while the NSA certainly has symmetric cryptanalysis capabilities that we in the academic world do not, converting that into practical attacks on the sorts of data it is likely to encounter seems so impossible as to be fanciful.
He thinks it's more likely they have some attacks against public-key crypto.
Breakthroughs in factoring have occurred regularly over the past several decades, allowing us to break ever-larger public keys. Much of the public-key cryptography we use today involves elliptic curves, something that is even more ripe for mathematical breakthroughs. It is not unreasonable to assume that the NSA has some techniques in this area that we in the academic world do not. Certainly the fact that the NSA is pushing elliptic-curve cryptography is some indication that it can break them more easily. If we think that’s the case, the fix is easy: increase the key lengths.
Today we learned that the NSA has apparently hacked something that lets them decrypt internet traffic. I'm guessing it's more likely they broke SSL/TLS rather than the underlying crypto. The story was published by both the NY Times, N.S.A. Foils Much Internet Encryption and The Guardian, US and UK spy agencies defeat privacy and security on the internet. The Guardian article includes some slides and some more tech talk but the NYT article puts things in perspective for a layman a little better. They summarize:
The N.S.A. hacked into target computers to snare messages before they were encrypted. In some cases, companies say they were coerced by the government into handing over their master encryption keys or building in a back door. And the agency used its influence as the world’s most experienced code maker to covertly introduce weaknesses into the encryption standards followed by hardware and software developers around the world.
“For the past decade, N.S.A. has led an aggressive, multipronged effort to break widely used Internet encryption technologies,” said a 2010 memo describing a briefing about N.S.A. accomplishments for employees of its British counterpart, Government Communications Headquarters, or GCHQ. “Cryptanalytic capabilities are now coming online. Vast amounts of encrypted Internet data which have up till now been discarded are now exploitable.”
The files show that the agency is still stymied by some encryption, as Mr. Snowden suggested in a question-and-answer session on The Guardian’s Web site in June. “Properly implemented strong crypto systems are one of the few things that you can rely on,” he said, though cautioning that the N.S.A. often bypasses the encryption altogether by targeting the computers at one end or the other and grabbing text before it is encrypted or after it is decrypted.
N.S.A. documents show that the agency maintains an internal database of encryption keys for specific commercial products, called a Key Provisioning Service, which can automatically decode many messages. If the necessary key is not in the collection, a request goes to the separate Key Recovery Service, which tries to obtain it. How keys are acquired is shrouded in secrecy, but independent cryptographers say many are probably collected by hacking into companies’ computer servers, where they are stored. To keep such methods secret, the N.S.A. shares decrypted messages with other agencies only if the keys could have been acquired through legal means. “Approval to release to non-Sigint agencies,” a GCHQ document says, “will depend on there being a proven non-Sigint method of acquiring keys.” Simultaneously, the N.S.A. has been deliberately weakening the international encryption standards adopted by developers. One goal in the agency’s 2013 budget request was to “influence policies, standards and specifications for commercial public key technologies,” the most common encryption method.Cryptographers have long suspected that the agency planted vulnerabilities in a standard adopted in 2006 by the National Institute of Standards and Technology and later by the International Organization for Standardization, which has 163 countries as members.
They also have two nice additions. They have the budget request and briefing sheet documents with some highlights and translations into regular english. Documents Reveal N.S.A. Campaign Against Encryption. They have an infographic trying to explain to the average user where the security protocols are used in the applications they run, Unlocking Private Communications.
So while some encrypted mail companies have shutdown, Developers Scramble to Build NSA-Proof Email.
Meanwhile the Patriot Act author says NSA’s bulk data collection is “unbounded in its scope”.
In one of the most prominent legal challenges to government intelligence gathering since the Edward Snowden disclosures, the American Civil Liberties Union (ACLU) has filed a lawsuit against four top Obama Administration officials. The case, known as ACLU v. Clapper, asks a federal judge to declare the entire metadata sharing program unlawful, halt it, and purge all related records.
On Thursday, Rep. James Sensenbrenner (R-WI), with representation from the Electronic Frontier Foundation (EFF), filed an amicus brief with the court. He noted that the vast data handover is not at all what Congress intended to happen. And Sensenbrenner should know, too, because he authored the Patriot Act in October 2001 and supported its subsequent reauthorizations.
Bruce Schneier outlines The Only Way to Restore Trust in the NSA.
The NSA has repeatedly lied about the extent of its spying program. James R. Clapper, the director of national intelligence, has lied about it to Congress. Top-secret documents provided by Edward Snowden, and reported on by the Guardian and other newspapers, repeatedly show that the NSA's surveillance systems are monitoring the communications of American citizens. The DEA has used this information to apprehend drug smugglers, then lied about it in court. The IRS has used this information to find tax cheats, then lied about it. It's even been used to arrest a copyright violator. It seems that every time there is an allegation against the NSA, no matter how outlandish, it turns out to be true.
All of this denying and lying results in us not trusting anything the NSA says, anything the president says about the NSA, or anything companies say about their involvement with the NSA. We know secrecy corrupts, and we see that corruption. There's simply no credibility, and -- the real problem -- no way for us to verify anything these people might say.
It's time to start cleaning up this mess. We need a special prosecutor, one not tied to the military, the corporations complicit in these programs, or the current political leadership, whether Democrat or Republican. This prosecutor needs free rein to go through the NSA's files and discover the full extent of what the agency is doing, as well as enough technical staff who have the capability to understand it. He needs the power to subpoena government officials and take their sworn testimony. He needs the ability to bring criminal indictments where appropriate. And, of course, he needs the requisite security clearance to see it all. We also need something like South Africa’s Truth and Reconciliation Commission, where both government and corporate employees can come forward and tell their stories about NSA eavesdropping without fear of reprisal.
Trust is essential for society to function. Without it, conspiracy theories naturally take hold. Even worse, without it we fail as a country and as a culture. It's time to reinstitute the ideals of democracy: The government works for the people, open government is the best way to protect against government abuse, and a government keeping secrets from is people is a rare exception, not the norm.
Schneier also wrote The US government has betrayed the internet. We need to take it back.
By subverting the internet at every level to make it a vast, multi-layered and robust surveillance platform, the NSA has undermined a fundamental social contract. The companies that build and manage our internet infrastructure, the companies that create and sell us our hardware and software, or the companies that host our data: we can no longer trust them to be ethical internet stewards. This is not the internet the world needs, or the internet its creators envisioned. We need to take it back. And by we, I mean the engineering community.
One, we should expose. If you do not have a security clearance, and if you have not received a National Security Letter, you are not bound by a federal confidentially requirements or a gag order. If you have been contacted by the NSA to subvert a product or protocol, you need to come forward with your story. Your employer obligations don't cover illegal or unethical activity. If you work with classified data and are truly brave, expose what you know. We need whistleblowers.
We need to know how exactly how the NSA and other agencies are subverting routers, switches, the internet backbone, encryption technologies and cloud systems. I already have five stories from people like you, and I've just started collecting. I want 50. There's safety in numbers, and this form of civil disobedience is the moral thing to do.
Two, we can design. We need to figure out how to re-engineer the internet to prevent this kind of wholesale spying. We need new techniques to prevent communications intermediaries from leaking private information.
Three, we can influence governance. I have resisted saying this up to now, and I am saddened to say it, but the US has proved to be an unethical steward of the internet. The UK is no better. The NSA's actions are legitimizing the internet abuses by China, Russia, Iran and others. We need to figure out new means of internet governance, ones that makes it harder for powerful tech countries to monitor everything. For example, we need to demand transparency, oversight, and accountability from our governments and corporations.
To the engineers, I say this: we built the internet, and some of us have helped to subvert it. Now, those of us who love liberty have to fix it.
And of course, after reading all of these articles and writing the above, the best article is the last one I got to. Of course it's also by Bruce Schneier, who apparently is now working with Greenwald. While it's titled How to remain secure against NSA surveillance it also provides the best description I've seen of what we know about the NSA's capabilities. I won't even try to summarize or pull quotes from it.
More on Syria
McClatchy reports Intercepted call bolsters Syrian chemical-weapons charge, Germans say "According to Der Spiegel, one of the parties in the intercepted phone call was a ‘high-ranking member of Hezbollah,’ the militant Lebanese movement that’s sent fighters to support the Assad government. That Hezbollah member told the Iranian that ‘Assad had lost his temper and committed a huge mistake by giving the order for the poison gas use,' according to the magazine’s account."
"But the German account and the American one suggest that the inability of Assad’s regime to take control of the eastern Damascus suburbs after months of attempts drove a decision to use chemical weapons. An unclassified French intelligence summary also suggested that the failure to unseat the rebels lay behind the Aug. 21 attack. It called the use of chemical weapons followed by a ground offensive “a classic tactical scheme” consistent with Syrian military doctrine."
"The German account goes further than others that have been released recently in providing details of Assad’s state of mind that might have played a role in the motivation for launching a chemical attack, noting that Assad sees himself embroiled “in a crucial battle for Damascus.” It also said Assad’s forces had used a highly diluted chemical agent in previous attacks on rebels and that the high death count Aug. 21 might have been the result of “errors made in the mixing of the gas” that made it “much more potent than anticipated.” That would be consistent with a suggestion from an Israeli official, cited by The New York Times, that the attack was “an operational mistake.”"
Ezra Klein gives some history, Why Do We Even Care About Syria’s Chemical Weapons?
"The ban on chemical weapons, in other words, is proof that humanity can make war a little more decent. Consequently, its continued success is vital to all future efforts to make war a little more decent. There is a kind of beauty in that, but much less so when you recall the 100,000 Syrians killed by nonchemical weapons.
The U.S. is now debating a military campaign that marries the highest, most abstract idealism to the harshest, most unsettling pragmatism: Obama wants to punish Assad for violating the abstract norms of war even as he leaves Assad capable of continuing his massacre by more conventional means. This is why there is no enthusiasm for intervening in Syria: Making the decision to punish Assad means explicitly making the decision not to stop him. The brutality of what we are willing to accept tarnishes the better world we seek to preserve."
Ezra also wrote Why the very bad arguments for intervening in Syria matter which might be my favorite piece on the topic so far.
"I spent much of Wednesday reading through the transcript of the Senate Foreign Relation’s Committee’s four-hour hearing on Syria. All I could think was, “Good ideas do not need lots of lies told about them in order to gain public acceptance.” Longtime blogosphere obsessives will remember that line. Daniel Davies wrote it in 2004, in a justly famous blog post about the Iraq War. His point was that if the Iraq war was such a good idea, its proponents wouldn’t need to tell so many false stories about why they were doing it and what it would accomplish to win over the public."
The rest is good, going over the arguments used in the hearings. Read it.
Lydia DePillis spoke with Anthony Cordesman, A military expert explains how Syria missile strikes might actually work.